Single Sign On
- Single Sign-On (SSO) for applications with supported identity providers.
Overview
- This is applicable only if you are using services by any of the standard enterprise IAM providers listed below.
- Identity providers currently supported for SSO access to our platform:
- This integration allows access to our platform with the same credentials used to access your enterprise software.
- Pre-requisite: You need to register your identity (as an application) and the corresponding identity provider in our platform.
Benefits:
- No need to register for a SmartClean account to access our services.
- Your Property Administrators can invite users to your property using their email id registered with the IAM provider
Steps involved:
- Contact your SmartClean account representative to initiate the SSO integration setup.
- Create an OpenID Connect (OIDC) application with supported IAM provider and give us:
- Application ID and corresponding Secret Key
- Discovery URL
- We will whitelist the Discovery URL (domain of this IAM provider) to allow sign-in to our platform.
- Matrix will integrate with your IAM and request the following scopes when authentication required:
- Open ID
- Email ID
Outcome:
After the setup process is completed:
- Please choose your IAM provider when signing in to our platform.
- You will then be redirected to sign in with the IAM provider.
Authorization mechanism used:
- This process is based on an industry standard authorization mechanism: OAuth2
- Specific type: Authorization Code grant with PKCE extension.
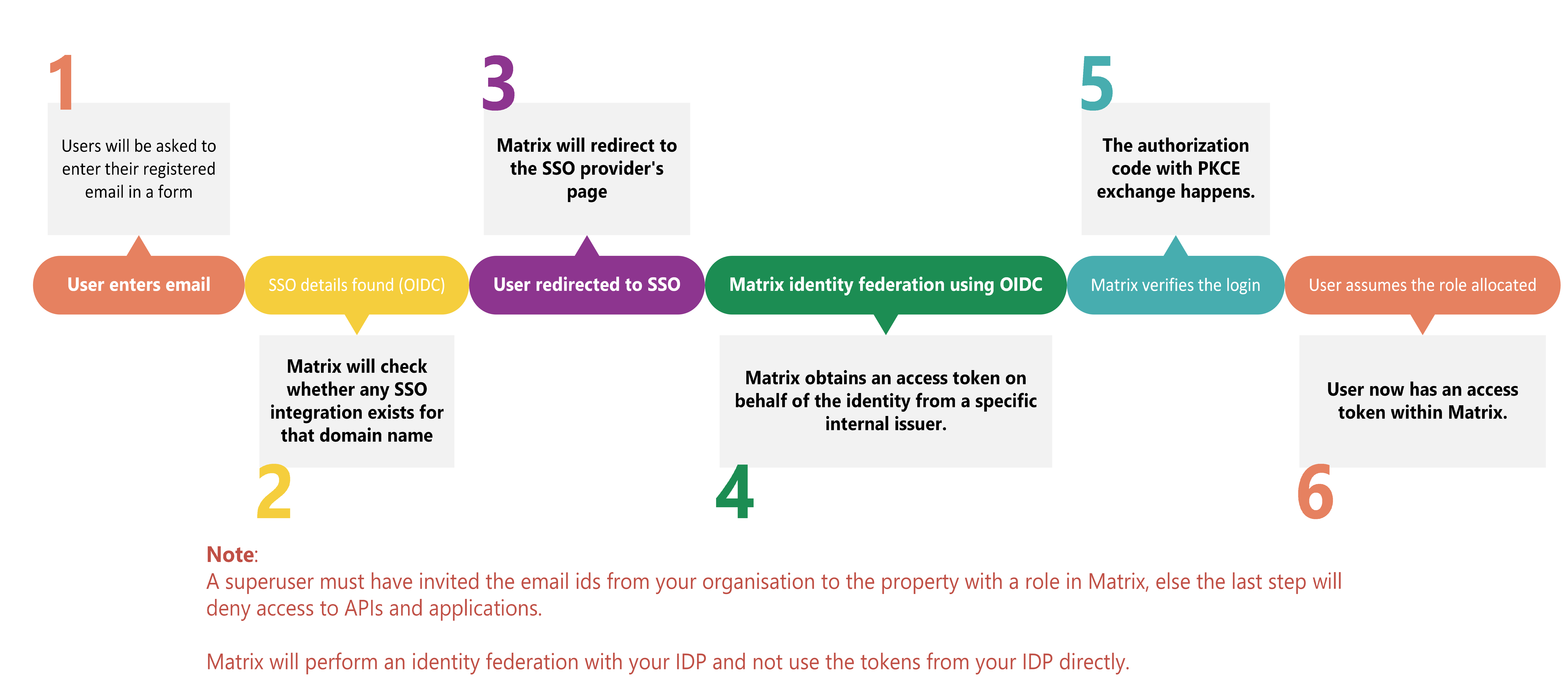
Process flow:
The diagram below shows the typical process flow from a user’s perspective.
Can I configure the token validity durations for my configuration ?
If your organisation security policies require your users to have a certain duration of tokens received for any application, this can be configured while onboarding your SSO in Matrix.
By default, the refresh as well as the access tokens will be valid for 3600s.
Note: This process is also involved in one of the standard options we provide for integration with external systems:
Introduced in the page: Integration based on identity federation